7 Cybersecurity domains you must know before you kickstart your career
Learn about different Cybersecurity disciplines to plan for the best-suited career and understand what would be the day in each of these field look like.
In this issue, I’ll explain the seven most popular Cybersecurity domains you should learn about before you begin your journey in the Cybersecurity. After learning about all Seven Cybersecurity disciplines, you can focus on a specific path and save huge amounts of money and valuable time.
Unfortunately, many cybersecurity enthusiasts quit their plans without getting a job.
Why do people fail?
Hype: People come across several Facebook/Instagram ads or Youtube Videos that talk about how learning Hacking can bring them a high-paying job in no time. This sounds lucrative to many individuals and they think learning Hacking is the only way to get into Cybersecurity career but unfortunately, they get trapped in a crowded town and fail.
Acquire unwanted Skill: Most people start with learning Windows hacking, Android hacking, CCTV hacking, etc but in the real world, this is usually not expected from Cybersecurity professionals and when they realize this, they get frustrated and stop exploring further.
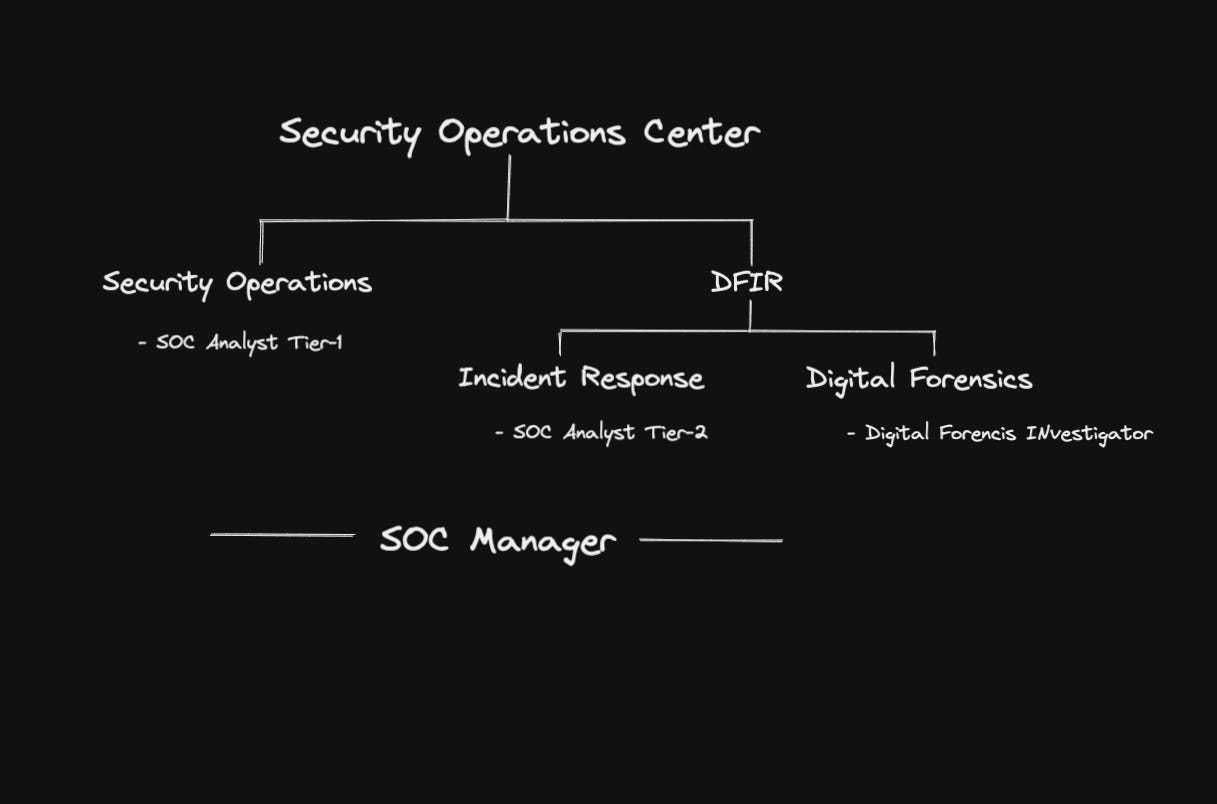
1. Security Operations, Incident Response, and Digital Forensics
What is the Security Operations domain?
When we talk about Security operations, we’re talking about the people on the cybersecurity front lines. These folks are responsible for day-to-day security management, monitoring, triage, and initial response to cyber attacks.
Incident response team is responsible for the eradication of threats from the network.
Digital Forensics team is responsible for investigating the origins & impacts of an attack.
This domain is collectively called Blue Team.
Different Roles and Required Skills
📌SOC Analyst Tier-1: They are dedicated to monitoring the most recent alerts and finding their urgency.
📌SOC Analyst Tier-2(Incident Responder): They are responsible for addressing real security incidents by evaluating incidents identified by Tier-1 analysts. They respond to incidents, minimize the impact and recover from security events.
📌Digital Forensic Investigator: They examine system data, user activity, and other pieces of digital evidence to determine if an attack is in progress and who may be behind the activity.
📌SOC Manager: Manages and prioritizes each action during different phases of the security operation center including detection, Eradication, analysis, containment, etc. SOC Managers are also responsible for communicating with different stakeholders during any high-severity incidents.
Note: Some organizations have combined Incident response & Digital forensics team, called DFIR(Digital Forensics & Incident Response).
DFIR professionals are required to have combined skills in both fields.
Who should plan for this domain?
Freshers: If you’re fresher and want to get into Cybersecurity, then you can prepare for Tier-1 SOC Analyst or Security Operations analyst however, zero experience can still be an obstacle and for that, you can read my past article on “How to break into Cybersecurity for complete beginner“
Experienced Professional: If you already have regular IT experience such as Network Support, Software Support, helpdesk support then you can definitely leverage those experiences in this domain.
2. Security Architecture and design
What are Security Architecture and design domain?
Security architecture and design teams are responsible for specifying, designing and implementing security controls and technologies.
Security Controls are tools or solutions to mitigate the risks such as Antivirus, Firewall, Spam filter, Web filtering solutions, Web Application firewall, security awareness training, etc
Security architects interact with non-security and often non-technical people to ensure that their designs meet business needs.
Different Roles and Required Skills
📌Security Architect: They run several enterprise security programs such as system hardening, security refresh, network segmentation, etc.
They also identify and recommend changes in policies, standards, established architecture, and best practices where necessary to further enhance enterprise security posture.
The required skills are — knowledge of Risk assessment, different cyber threats, security baseline, security compliances, and framework. Management skills are a plus.
📌Cloud Security Architect: They conduct security programs for Cloud environments such as AWS Cloud, Microsoft Azure, Good Cloud, Oracle Cloud, IBM Cloud, etc.
The required skills for this role are— Knowledge of AWS or Azure or GCP services, understanding of Cloud security compliances such as Cloud Security alliance framework, PCI DSS, etc
Who should plan for this domain?
Fresher: Unfortunately, freshers cant apply for these roles as Security architect roles require at least 5-6 years of security experience.
Experience: If you’ve around 5-6 years of experience in Security Operations & Incident response then you’re definitely eligible for this role.
3. Security Assessment
What is an Application security domain?
Very often when people think of Cybersecurity, they think of Ethical Hacking a.k.a Penetration Testing.
While Penetration Testing role falls within Security assessment domain, this discipline comprises many functions beyond just penetration testing.
Security Assessment includes several sub-domain that focus on detecting and eliminating security weaknesses. The scope of these activities can include network devices, servers, computers, web applications, physical security, personnel etc
What are the different roles in it?
📌Vulnerability Management Engineer/Security Analyst: They conduct periodic automated scanning of organizations’s assets such as Routers, Switches, Firewalls, Web Applications, etc to find security weaknesses. In most organizations, this is usually combined with other security roles.
📌Penetration Tester: They Assess IT Infrastructure within the defined scope by using attacker-style techniques to detect and report weaknesses before the real attacker could do. They use both automated tools and hands-on technical hacking. These activities are also called Red Team exercises.
Who should opt for this domain?
Fresher: It is difficult to get into Security Assessment role directly however, you could begin with Security Internship and then start looking for Junior Penetration Tester or Security Analyst role.
Experienced: If you’ve spent 2-3 years in Cybersecurity or Software Testing or software development, you might get a smooth transition to a Penetration Testing role and if you’ve 2-3 years of experience with IT Network or Support role, you can plan for Vulnerability Management or Security Analyst role.
3. Application, Software, and Product Security
What is an Application Security domain?
Application Security domain is developed by organizations to secure their Internal application and also to offer Support Services to their customers.
Application security is usually integrated within the Software development life cycle(SDLC). It is all about detecting security issues on software in the early stage or during the development process itself.
What are the different roles in it?
📌Application Security Auditor: They are responsible for conducting a security audit of Web Applications using tools such as SAST(Static application security testing) and DAST(Dynamic application security testing).
📌DevSecOps Engineer: DevSecOps engineers closely work with DevOps team and developers will receive automated output on the application security status, detailing what issues need to be fixed.
Who should plan for this domain?
Fresher: Unfortunately, this domain is not suited for Freshers.
Experienced: If you’ve 2-3 years of experience in Software QA Testing, Software development, or DevOps environment, these roles are best-suited for you.
5. Governance and Compliance
What is a Governance and Compliance domain?
It is the job of the governance and compliance team to ensure that all areas of the organization are compliant with external regulations and internal policies such as
PCI DSS Compliance - For organizations storing or processing Payment cards
HIPPA Compliance - For organizations storing or accessing the Health Information of Patients in the United States
GDPR - For Organizations serving customers in the European region
What are the different roles in it?
GRC Analyst: Responsible for maintaining security compliance and preparing routine reports. Also evaluate risks — known and unknown — within the company and its operations in accordance with known industry frameworks (ISO, NIST, etc.)
They also review, modify, and maintain existing practices and policies to reflect our operations and values within specific industry-standard frameworks (i.e. ISO, NIST)
Who should opt for this domain?
Fresher: Luckily, there are some Junior GRC Analyst roles available in the market for complete freshers but you need to be good at Security compliances and frameworks.
Experienced: If you’ve spent 2-3 years in Security Architect role or Security Manager role, you could easily get into GRC Analyst or Specialist roles.
Conclusion
After learning about all the popular domains, you might get a basic understanding of what domain is right for you. If you ask me, I’d recommend planning for either Security Operations or Security Assessment domain as these have got the most number of unfilled opportunities.